EncryptedRegView 17.12 Crack Activation Free (Final 2022)
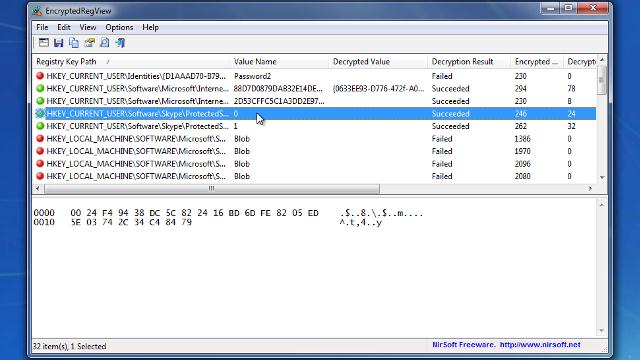
EncryptedRegView makes it possible for you to analyze either the computer's registry or the registry of an external drive, and find the keys that are encrypted using the Data Protection API (or, in short, DPAPI). It is not a standard registry explorer, but a tool that can help you dig deeper into the registry and search for entries that are not normally displayed.
Analyze either the local registry or an external drive
Upon launch, you must go through the advanced options to select the target to scan (local or external). Choosing an external drive requires you to fill in the location of the root folder, the registry hives, the user and the classes registry files. Automatic filling is also possible for a given root directory. To decrypt system protected data, administrator rights are mandatory.
Once you hit the 'OK' button, EncryptedRegView starts scanning the registry, displaying the data it finds key by key in a structured manner. Aside from the path of each registry key, EncryptedRegView discloses both its encrypted and decrypted values. Also, it displays the decryption status, the length of the encrypted and decrypted data, the hash and the encryption algorithm that was used. Clicking on any key reveals the hex-coded form of the key.
Advanced selection and reporting options
EncryptedRegView features satisfactory reporting tools, which enable you to save selected chunks of data in various formats, namely TXT, CSV, HTML, or XML. HTML reporting is also available in the right-click menu.
The advanced selection tools can assist you in choosing the data you want to export. As such, you can select the rows you want to include in the report (and there are options to choose even or odd rows with a click, so you don't have to do this manually), and eliminate the columns you don't want the report to contain.
Decrypt data within the system's registry
EncryptedRegView can disclose encrypted data that can contain passwords for both Microsoft or third party products. It scans the system without modifying the registry, placing all the information within an organized table, for your convenience.
Download ⇒ DOWNLOAD (Mirror #1)
Download ⇒ DOWNLOAD (Mirror #1)
EncryptedRegView Free X64 (2022)
EncryptedRegView is a free and open-source tool for Windows which allows you to detect the keys that are protected by Data Protection API (DPAPI). If any keys from the system are protected by DPAPI, EncryptedRegView is able to display the encrypted key value, along with a key information.
Want to change your region?
Whether you are creating a video or a film, or are preparing a manuscript, screenplays, stories, TV shows or other, you need to use a certain font, and it’s a pain to always change back and forth between the default fonts. Sometimes you’re working with someone who’s got the same situation, but the last person to edit the document used a different font, and now it’s bothering you.
Ensuring that the rights to your work are being protected is one of the most important aspects of your work.
This guide is devoted to fixing some frequently asked questions about EncryptedRegView (EVR), an open-source utility written in C++ that encrypts data inside the Windows Registry. It allows users to analyse data inside Windows Registry that is encoded using the Data Protection API (DPAPI).
You can download EncryptedRegView from the links below.
What is EncryptedRegView?
EncryptedRegView is a free and open-source utility that enables Windows users to analyse data inside Windows Registry that is encoded using the Data Protection API (DPAPI). It’s an open-source project. The source code of the project is hosted on GitHub. If you want to see exactly how the project was written and what coding skills were required, you can check out the code repository’s README file.
What can EncryptedRegView do?
EVR can encrypt and decrypt registry keys and values, as well as open the registry in XML format and retrieve key and value information.
Features
– Read and display encrypted registry data
– Display values that are encrypted with the Data Protection API
– Find out if the registry key is encrypted
– Analyse the registry keys and values
– Option to automatically fill in registry hives
– Read and display the registry keys that have an SACL with an owner that matches your own user account
– Option to write encrypted keys or values to the registry
– Option to read encrypted values from a network share
– Option to analyse encrypted values
– Export your encrypted registry data in various formats, including HTML
– Option to analyse encrypted data in the system’s registry without modifying it
EncryptedRegView Crack Full Version
We use this value to see if a key is a known system key. In Windows versions that use the UPX (Ultimate Packer for eXecutables) format, this value is set to the UPX part number, e.g. 4090. This is a very weak indicator and can easily be modified by malicious software. If a given key is not known to the program, it will be marked as an unknown key.
KEYDEFER Description:
This value is the ‘deferred’ part of the key. If the default action for this key is ‘deferred’, it means that the key’s data should be recovered before the key is evaluated.
KEYPREFIX Description:
This value is the ‘prefix’ part of the key. It is similar to the KEYMACRO key, but we do not care if the key is the UPX part number (i.e. 4090), we only care if the key is included in the encryption-enabled registry.
KEYNAME Description:
This is the ‘name’ part of the key, which is what the user sees.
KEYTYPE Description:
This is the ‘type’ part of the key, which tells us the kind of key that it is.
KEYVALUE Description:
This is the ‘value’ part of the key, which is a (hex) string that the user sees.
KERBALED Description:
This value is the ‘kerbaled’ part of the key, which tells us whether the key is stored in the Windows Registry (0) or in a file (1).
KERBEROS Description:
This value tells us whether this key is protected by kerberos, or how kerberos is used to encrypt the key. This value is only set if the key is kerb-protected.
KERBEROSDESCRIPTION Description:
This value is a textual description of the key’s kerberos protection.
KERBEROSKEYDESCRIPTION Description:
This value is a textual description of the key’s kerberos protection.
KERBEROS_DOMAIN Description:
This value is the kerberos domain (computer) the key is from, which is used to decrypt the key.
KERBEROS_HOSTNAME Description:
This value is the kerberos host name that decrypts the key.
KERBEROS_HOST_NAME Description:
This value is the kerberos host name that decrypts the key
a86638bb04
EncryptedRegView Crack + Download
Password recovery tools
Registry entries analysis
Registry Export
Registry Report
Registry Scan
Registry Search
Password Recovery
Password Reset
Registry Export
Upon installation, you must select a directory to export the registry key information to. The export can be in any file format. The tool supports XML, TXT, and CSV. All reports can be exported in different formats, such as XML, HTML, and CSV. You can further select the output format using the right-click context menu.
Additionally, you can save the exported information in any file format. The export can be in XML, TXT, CSV, or HTML. Also, you can choose the format of the export. Upon saving, the tool encodes the data with the help of encryption algorithms. Encryption algorithms used by EncryptedRegView are based on Data Protection API (DPAPI).
Registry Entry Analysis
Registry analysis can be helpful in a variety of situations. In the first place, it is useful if you want to analyze the source code of the Windows registry itself, as it can enable you to find out the registry keys associated with the Windows Registry. This is a particularly handy technique when you want to find out the registry keys associated with a file.
Other applications that use the Registry include programs that display registry paths, which can make you change the settings of a certain file. In this case, you can use the information provided by the tool to obtain the registry path of the file.
Registry Export
Once you have found the registry keys of a certain file, you can export them to an easily accessible file format. The Export option can save the registry key information in a TXT, CSV, or HTML file. To do so, simply select the registry keys you want to include in the report, and then choose the appropriate export format.
Registry Report
Sometimes you don’t want to export the registry keys to a file, but rather analyze them in the application that reads them. If you are such a person, you can take advantage of the Registry Report feature. This feature allows you to analyze the registry keys of either the computer’s registry or the registry of an external drive. To do so, choose the target to scan (local or external) and select the option to create a report. Then, select the type of report you want to create.
Registry Scan
Use the Registry Scan feature to check if the registry keys you want to analyze
What’s New in the?
https://techplanet.today/post/catalogo-unificado-edifil-pdf-download-link
https://techplanet.today/post/windows-xp-sweet-62-fr-driver-sata-iso
https://new.c.mi.com/ng/post/78909/NLite_V147_Portable_64_Bit_UPD
https://new.c.mi.com/my/post/475191/Oblivion_Drum_Kit_WAV
https://techplanet.today/post/chicken-invaders-5-crash-fix-working-multiplayer-full-work-version
https://new.c.mi.com/my/post/472464/Realtek_11n_Usb_Wireless_Lan_Utility_Version_700_D
https://techplanet.today/post/x360celib64r848vs2010zip
https://new.c.mi.com/ng/post/77422/Html5_Radio_Player_Nulled_38_VERIFIED
https://new.c.mi.com/th/post/1434894/Crys3_Dll_WORK_Download_Free
https://new.c.mi.com/ng/post/78904/Ghajini_720p_Download___TOP
https://techplanet.today/post/stoik-smart-resizer-3-registration-key
https://new.c.mi.com/th/post/1441393/FULL_Elcomsoft_Password_Recovery_Bundle_Forensic_2
https://techplanet.today/post/kerio-control-web-filter-license-verified-crack
https://techplanet.today/post/contoh-soal-tes-tertulis-bank-muamalat-gratis-link
https://new.c.mi.com/th/post/1440992/LucisArt_Version_3_ED_SE_Photoshop_Plugin_Windows_
https://techplanet.today/post/wondersharedrfonetoolkitv920crack-top
https://new.c.mi.com/my/post/472459/If_My_Heart_Had_Wings_-Flight_Diary-_-_New_Wings_A
https://techplanet.today/post/windows-81-display-drivers-wddm-11-new-download
https://techplanet.today/post/dulhe-raja-exclusive-full-movie-download-720p-hd
https://techplanet.today/post/callofdutymodernwarfare4fullgamemp-sp-aviara-upd
https://techplanet.today/post/sencor-dvb-t-usb-stick-driver-top-downloadl
https://new.c.mi.com/ng/post/77166/2021_Free_Word_To_Ieee_Format_Converter_Onlineepub
https://new.c.mi.com/global/post/491453/Conrad_Fischer_100_Cases_Of_Medical_Ethics_Pdf_60_
https://techplanet.today/post/neyrinck-v-control-pro-cracked-tongue-exclusive
https://techplanet.today/post/kitchendraw-65-torrent-high-quality
https://new.c.mi.com/global/post/491448/Embriologia_Medica_Longman_12_Edicionpdf_NEW
https://new.c.mi.com/ng/post/77417/Copytrans_Control_Center_Crack_Serial_UPDATED
https://jemi.so/ugly-in-hindi-full-exclusive-movie-download
https://new.c.mi.com/my/post/474287/EVEREST_Ultimate_Edition_5502100_Key_Serial_Key_BE
https://new.c.mi.com/global/post/492737/LS_Models_LS_Land_Issue_04_Fairyland_Rar
https://new.c.mi.com/th/post/1434889/Serioussam3lanfixcrack_TOP
https://techplanet.today/post/lone-survivor-hindi-dubbed-movievilla-updated
https://techplanet.today/post/borat2006720pbrripx264yifymp4
https://techplanet.today/post/koj-saka-da-bide-milioner-igra-download-added-by-requestl-install
https://new.c.mi.com/th/post/1438696/Solucionario_Ingenieria_Economica_Guillermo_Baca_C
https://jemi.so/hindu-young-world-quiz-book-free-better-90
https://techplanet.today/post/hd-online-player-descargar-waves-z-noise-zip
https://techplanet.today/post/resident-evil-6-fixer-102-169
https://techplanet.today/post/office-timeline-402-crack-plus-activation-key-2020-best
https://techplanet.today/post/free-download-gta-san-andres-resident-evil-dead-aim-link
https://new.c.mi.com/my/post/472439/Gad_Kille_Maharashtra_Pdf_Download_FREE
https://new.c.mi.com/my/post/474253/Altium_Designer_20013_Build_296_License_Key
https://new.c.mi.com/my/post/473215/Sam_Mechanism_Software_Crack_Tutorial_EXCLUSIVE
https://techplanet.today/post/burnout-paradise-vanity-pack-20-23l
System Requirements:
Minimum:
Mac OS X v10.6.8 (10A606)
Intel Macs with 2 GB of RAM
Windows 7 (64-bit)
Recommended:
Mac OS X v10.7 (10A716)
Intel Macs with 4 GB of RAM
https://kevinmccarthy.ca/puppetmaster-crack-license-code-keygen-download-for-pc/
http://naturopathworld.com/?p=23713
https://www.scoutgambia.org/dynamic-proxy-crack-activation-code-free-download/
http://subsidiosdelgobierno.site/?p=42807
https://parsiangroup.ca/2022/12/sonote-crack-with-license-code-free-download/
http://www.healistico.com/kp-timer-crack-torrent-free-download/
https://amnar.ro/katmouse-torrent-activation-code-free-x64-latest/
http://modiransanjesh.ir/bayesian-coin-tosser-crack-free-updated/
http://insenergias.org/?p=125254
https://werco.us/2022/12/09/office-communicator-sdk-wrapper-crack-free-win-mac-latest/
